| Version 2 (modified by , 14 years ago) (diff) |
|---|
An ARP spoofing experiment where the attacker puts himself in between two nodes and then modifies their traffic. There are two classes of experiments that need to be combined:
- an experiment where ARP poisoning happens between two nodes by the attacker
- an experiment where an attacker changes traffic passing through it
Example 3: ARP poisoning with MITM attack
This example used two metadescriptions. The first was ARP poisoning which is a flavor of cache poisoning, and the other is MITM attack. This example is written in [CurrentlyProposedLanguage].
ARP poisoning metadescription
This is a special case of cache poisoning where the target is ARP cache.
- Logical topology:
Objects:
Attacker extends Node
IP extends IPAddress
fakePA extends MACAddress
Cache extends Object
Cache := {ARPRecord[] records}
Cardinality:
|Attacker|1
|IP|1
|fakePA|1
|Cache|1
Relationships:
not collocated(Cache, Attacker)
- Timeline of events:
Definitions:
Attacker a, IP ip, fakePA fpa, Cache c
e1 := {type = ARPREPLY, origin = a, destination = c, content = (ip = fpa)}
s1 := {c.records += (ip = fpa)}
Timeline:
e1 -> s1
- Invariants:
Nothing in addition to the topology and timeline above.
MITM attack metadescription
Dimensions:
- Logical topology:
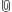
(in English: There is one attacker node, and two regular nodes who want to communicate. These are all different nodes.)
- Timeline of events:
(in English: Attacker replaces each msg between nodes with some modification.)
- Invariants:
Nothing in addition to the topology and timeline above.
Experiment design
Now I'm a user who wants to design an experiment. I need to combine two metadescriptions (ARP poisoning and MITM attack) and somehow tie them down to generator choices. To combine I'll do something like this:
i.e. the ARP experiment needs to be run twice to generate the mappings at node1 and node2 necessary for the attacker to appear on the path from node1 to node2. The cache we're poisoning is at node1 and node2. Poison links the IP address of node2 and node1 respectively with the attacker's ARP address.
The system now needs to offer me several generators:
- It should offer a topology generator and map the nodes (Node1, Node2, Attacker) to the topology that gets generated. Caches have to reside at Node1 and Node2.
- It should offer event generator for each of the events: reply (for ARP), and mod(for message).
