| Version 42 (modified by , 13 years ago) (diff) |
|---|
You are now rockin with the west
An Exercise in Anonymity
Step 1 Setting Up the Network
Swap in the Experiment using this NS file
Then log in to users.isi.deterlab.net through Putty. For help on logging onto Putty check out this tutorial.
Setting up apache
We need to generate traffic in our network and one of the easiest ways to do that is with HTTP traffic, so we need to set up a server and a web page. Connect to Server 1 and use the command: sudo /proj/DeterTest/runme.nodeA This will run a script with Apache 2 which sets up the server and web page and displays the users IP address on the Server 1 node. When prompted "Do you want to continue [Y/n]?" select Y Once the script is done running, the server is now set up and we can generate traffic! You can check this by typing w3m http://localhost/cgi-bin/ip.cgi which should display your IP address.
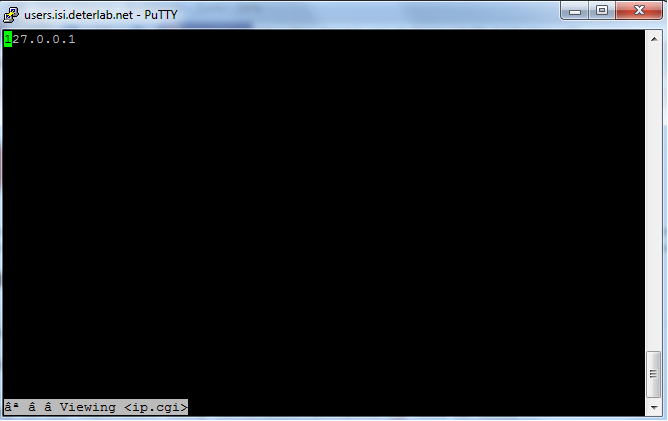
It should look like this. Repeat this process on Server 2
Setting up the proxy node
Log onto the proxy node and use the command: sudo /proj/DeterTest/runme.proxy this will run a script which installs and sets up tinyproxy on the node. The proxy is now set up! We'll get to using it in a little while.
Step 2 Viewing Network Traffic
We are now ready to begin learning! One person needs to connect to either Alice while another person logs into the server1 node (or server2 if you choose). From the server node type the command ifconfig This will show the ethernet links that the node is using.
Find the one that shows an inet address of 10.x.x.x In the example above it is eth0. Yours may be different, but that is still ok.
Then type the command sudo tcpdump -i eth0 -s 0 -x -w /tmp/tcpdump.pcap This will begin listening to the traffic that comes through this node and that specific ethernet link, eth0 in the example, and write the data out to the file tcpdump.pcap in the tmp diretory. At this time, the person connected to Alice will enter the command wget http://server1/cgi-bin/ip.cgi This saves a local copy of the web page set up on the server, and by doing so generates HTTP traffic to examine.
Attachments (24)
- Walk Through.docx (353.0 KB) - added by 13 years ago.
- wan.php3 (692 bytes) - added by 13 years ago.
- apache2setup.png (34.3 KB) - added by 13 years ago.
- sshclientlogon.png (91.0 KB) - added by 13 years ago.
- sshclientstart.png (62.1 KB) - added by 13 years ago.
- wireshark.png (111.7 KB) - added by 13 years ago.
- networksetup.png (18.9 KB) - added by 13 years ago.
- wiresharkdirect.png (93.7 KB) - added by 13 years ago.
- wiresharkthroughproxy.png (104.2 KB) - added by 13 years ago.
- wiresharkthroughtor.png (112.9 KB) - added by 13 years ago.
- ifconfig.2.png (58.3 KB) - added by 13 years ago.
- ifconfig.png (68.7 KB) - added by 13 years ago.
- ifconfig.3.png (68.7 KB) - added by 13 years ago.
- readwireshark.png (131.1 KB) - added by 13 years ago.
- Regular Dataflow.png (39.3 KB) - added by 13 years ago.
- Proxy Dataflow.png (42.7 KB) - added by 13 years ago.
- Tor Dataflow.png (43.0 KB) - added by 13 years ago.
- onion.png (23.9 KB) - added by 13 years ago.
- anonymous.2.ns (2.6 KB) - added by 13 years ago.
- anonymous.txt (2.6 KB) - added by 13 years ago.
- anonymous.ns (2.6 KB) - added by 13 years ago.
- tor_setup.tgz (5.6 KB) - added by 13 years ago.
- runme.apache (370 bytes) - added by 13 years ago.
- runme.proxy (280 bytes) - added by 13 years ago.
Download all attachments as: .zip

