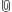
This page talks about language used to design experiments. It should both be used to design metadescriptions and perhaps to make them more specific to a particular experiment the user wants to run.
I'll start with a few examples of experiments first, that we should be able to design in this language.
We may end up with a single language or a set of related languages. Here is what we need to express:
Note that intentionally this is all pretty high-level and is orthogonal to any generator used to generate topologies, traffic, etc. There must be a mapping process that selects eligible generators for each dimension and takes their output and maps objects and events to it. More about this mapping process later.
I'll now ignore the question which language to use to design experiments because I think that pretty much any language can be used once we know what we want to say. To figure this out I'll try to use some variation of UML that can express both protocol diagrams and state transitions. If the level of detail is right we can decide on appropriate language in the next step.
This example used two metadescriptions. The first was ARP poisoning which is a flavor of cache poisoning, and the other is MITM attack.
This is a special case of cache poisoning where the target is ARP cache. I've highlighted customizations from the general cache poisoning metadescriptions to arrive at this one.
Dimensions:
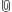
(in English: There is one attacker node. There is a fakeIP of type IPaddress. A cache is simply a collection of ARPRecord items, one or more. These are subtypes of Info and in the domain knowledge DB there's syntax defined for an ARPRecord. Cache does not reside at the attacker.)
(in English: Attacker sends the ARP reply with mapping of an ARP address to somebody's IP. This really could be anybody's ARP address but in most cases it is the attacker's.)
Nothing in addition to the topology and timeline above.
Dimensions:
(in English: There is one attacker node, and two regular nodes who want to communicate. These are all different nodes.)
(in English: Attacker replaces each msg between nodes with some modification.)
Nothing in addition to the topology and timeline above.
Now I'm a user who wants to design an experiment. I need to combine two metadescriptions (ARP poisoning and MITM attack) and somehow tie them down to generator choices. To combine I'll do something like this:
i.e. the ARP experiment needs to be run twice to generate the mappings at node1 and node2 necessary for the attacker to appear on the path from node1 to node2. The cache we're poisoning is at node1 and node2. Poison links the IP address of node2 and node1 respectively with the attacker's ARP address.
The system now needs to offer me several generators: